kubernetes实战
POD
运行POD
# 命令格式: kubectl run (pod控制器名称) [参数]
# --image 指定Pod的镜像
# --port 指定端口
# --namespace 指定namespace
kubectl run nginx --image=nginx:latest --port=80 --namespace dev
POD环境变量
apiVersion: apps/v1
kind: Deployment
metadata:
creationTimestamp: null
labels:
app: mysql-env-pod
name: mysql-env-pod
namespace: app-dev
spec:
replicas: 1
selector:
matchLabels:
app: mysql-env-pod
template:
metadata:
creationTimestamp: null
labels:
app: mysql-env-pod
spec:
containers:
- image: images.io:5000/app/mysql
name: mysql
env:
- name: MYSQL_ROOT_PASSWORD
value: "123456"
ports:
- containerPort: 3306
查看POD信息
# 查看Pod基本信息
[root@master ~]# kubectl get pods -n dev
NAME READY STATUS RESTARTS AGE
nginx 1/1 Running 0 43s
# 查看Pod的详细信息
[root@master ~]# kubectl describe pod nginx -n dev
删除POD
kubectl delete pod nginx -n dev
配置操作
创建一个pod-nginx.yaml,内容如下:
apiVersion: v1
kind: Pod
metadata:
name: nginx
namespace: dev
spec:
containers:
- image: nginx:latest
name: pod
ports:
- name: nginx-port
containerPort: 80
protocol: TCP
ConfigMap
创建ConfigMap对象的方法有两种
命令式命令
1.字面量:kubectl create configmap NAME --from-literal=key1=value1
2.从文件加载:kubectl create configmap NAME --from-file=[key=]/PATH/TO/FILE
3.从目录加载: kubectl create configmap NAME --from-file=[key=]/PATH/TO/DIR/
配置文件
1.命令式:kubectl create -f
2.声明式:kubectl apply -f
提示:基于文件内容生成时,可以使用命令式命令以dry-run模式生成并保存
查看帮助
kubectl create configmap -h
案例1:
kubectl create configmap my-cm --from-literal='test.html'='this is nignx' --dry-run=client -o yaml > my-cm.yaml
文件内容
apiVersion: v1
data:
test.html: this is nignx
kind: ConfigMap
metadata:
creationTimestamp: null
name: my-cm
案例2:
kubectl create cm my-cm2 --from-file=./map.txt --dry-run=client -o yaml >my-cm2.yaml
文件内容
apiVersion: v1
data:
map.txt: |
configmap
kind: ConfigMap
metadata:
creationTimestamp: null
name: my-cm2
引用ConfigMap对象
ConfigMap资源对象中以key-value保存的数据,在Pod中引用的方式通常有两种
- 环境变量
1.引用ConfigMap对象上特定的key,以valueFrom赋值给Pod上指定的环境变量
2.在Pod上使用envFrom一次性导入ConfigMap对象上的所有key-value,key(也可以统一附加特定前缀)即为环境变量名,value自动成为相应的变量值
- configMap卷
1.在Pod上将ConfigMap对象引用为存储卷,而后整体由容器mount至某个目录下;key转为文件名,value即为相应的文件内容
2.在Pod上定义configMap卷时,仅引用其中的部分key,而后由容器mount至目录下
3.在容器上仅mount configMap卷上指定的key
在Pod上配置使用ConfigMap示例
1.通过存储卷引用
apiVersion: apps/v1
kind: Deployment
metadata:
labels:
app: my-dep
name: my-dep
spec:
replicas: 1
selector:
matchLabels:
app: my-dep
template:
metadata:
labels:
app: my-dep
spec:
containers:
- image: nginx:latest
name: nginx
ports:
- containerPort: 80
volumeMounts:
- name: my-cm-configmap # 卷名称
mountPath: /usr/share/nginx/html/ # 容器内挂载路径
readOnly: true # 只读 否
volumes:
- name: my-cm-configmap # 卷名称
configMap:
name: my-cm # configmap名称
optional: false
2.通过环境变量引用
apiVersion: apps/v1
kind: Deployment
metadata:
labels:
app: my-dep
name: my-dep
spec:
replicas: 1
selector:
matchLabels:
app: my-dep
template:
metadata:
labels:
app: my-dep
spec:
containers:
- image: nginx:latest
name: nginx
ports:
- containerPort: 80
env:
- name: PORT
valueFrom:
configMapKeyRef:
name: my-cm
key: 'test.html'
optional: false
Secret
secret资源
1.Secret主要用于存储密钥、OAuth令牌和 SSH 密钥等敏感信息,这些敏感信息采用base64编码保存,略好于明文存储
2.Secret根据其用途等,还有类型上的区分
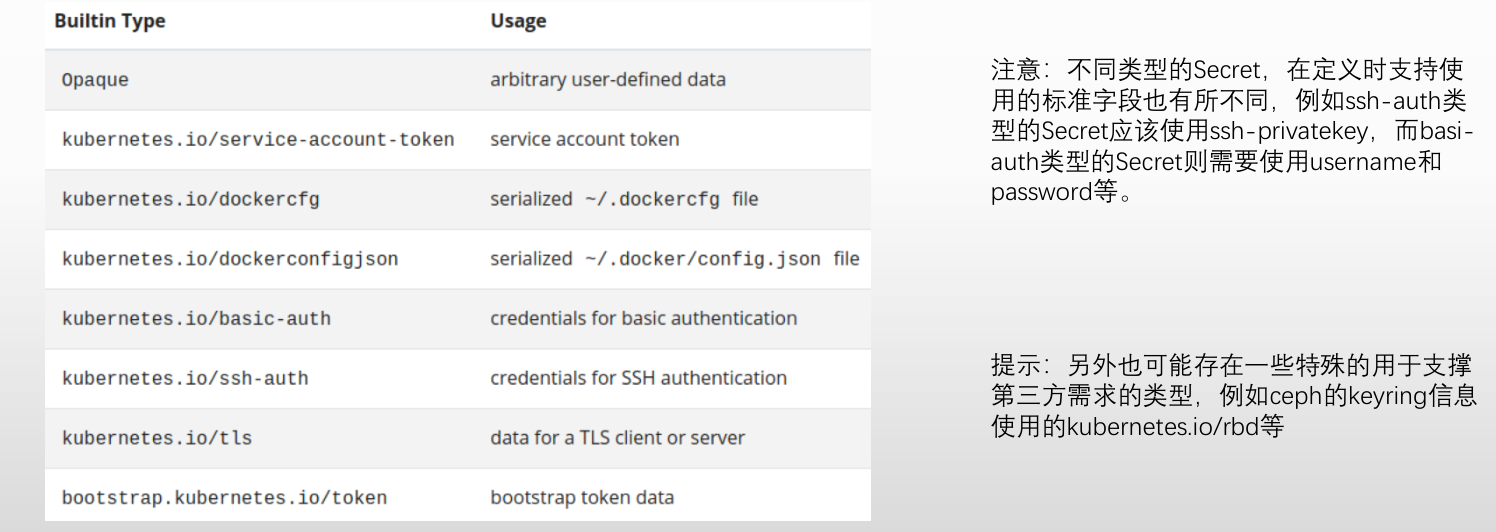
创建Secret资源
支持类似于ConfigMap的创建方式,但Secret有类型子命令,而且不同类型在data或stringData字段中支持嵌套使用的key亦会有所有同
命令式命令
#generic
1.kubectl create secret generic NAME [--type=string] [--from-file=[key=]source] [--from-literal=key1=value1]
2.除了后面docker-registry和tls命令之外的其它类型,都可以使用该命令中的--type选项进行定义,但有些类型有key的特定要求
#tls
1.kubectl create secret tls NAME --cert=path/to/cert/file --key=path/to/key/file
2.通常,其保存cert文件内容的key为tls.crt,而保存private key的key为tls.key
#docker-registry
1.kubectl create secret docker-registry NAME --docker-username=user --docker-password=password --docker-email=email [--docker-server=string] [--from-file=[key=]source]
2.通常,从已有的json格式的文件加载生成的就是dockerconfigjson类型,命令行直接量生成的也是该类型
资源示例
- 命令式
kubectl create secret generic mysql-root-auth --from-literal=username=root --from-literal=passwd=123456 --dry-run=client -o yaml
kubectl create secret tls my-tls --cert=./itshare.crt --key=./itshare.key --dry-run=client -o yaml
- 配置文件
apiVersion: v1
data:
passwd: MTIzNDU2
username: cm9vdA==
kind: Secret
metadata:
name: mysql-root-auth
apiVersion: v1
data:
tls.crt: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSURFVENDQWZrQ0ZEVjRpUFhjNlNIelR4a2NzdEwzTFUxRFRzTmNNQTBHQ1NxR1NJYjNEUUVCQ3dVQU1FVXgKQ3pBSkJnTlZCQVlUQWtGVk1STXdFUVlEVlFRSURBcFRiMjFsTFZOMFlYUmxNU0V3SHdZRFZRUUtEQmhKYm5SbApjbTVsZENCWGFXUm5hWFJ6SUZCMGVTQk1kR1F3SGhjTk1qTXdOakl6TVRZeU1qQTJXaGNOTWpRd05qSXlNVFl5Ck1qQTJXakJGTVFzd0NRWURWUVFHRXdKQlZURVRNQkVHQTFVRUNBd0tVMjl0WlMxVGRHRjBaVEVoTUI4R0ExVUUKQ2d3WVNXNTBaWEp1WlhRZ1YybGtaMmwwY3lCUWRIa2dUSFJrTUlJQklqQU5CZ2txaGtpRzl3MEJBUUVGQUFPQwpBUThBTUlJQkNnS0NBUUVBelFPZEZodlNlejJVNEZVK3lIaU1qT3BCWHhVd0RiV1NScW5GaUFMenc3OFk0bmx1Cmw3MFFzeGlTNEdndFJKK1JwZlRuSEF5RTVmNUxnS2lCc0U1WS9IdlQ5NDZSWEZZYVEyOTBNYTNSbFY3b3V3ODMKUmVTZmg0ZWI2cmlKVW00eVBYaUxUZHRmNXF2K2FuZGtFdVZ1VlFaMUpOVUxoRFF0dzRFQ1J4eURvc0s1R1VHVApmYVpGczByVUdMQTV1Ui8zVHM2b1hxWnowUkZYVC9lU29JbEFnMVplckpHd0FlNTNhWllvdm9ERi9Ja2lubldOCjB3Y2dQSWl4R1RtdU9iQ0NPS3k1bk8xMnJ5NGtFa3djRWRkSkQ2S3JKYkdYNkg3VWNXV3VvQkxUUDhoVEgxTjEKNUtIVmtJZ0U2a3h4RHpVeUtNb3FhekZ3M0MrVUp5U0pEZHVnb3dJREFRQUJNQTBHQ1NxR1NJYjNEUUVCQ3dVQQpBNElCQVFBcE40OHlWTml3RnR4TEZ5V3ZVTmdQRWZLc0c1M3M2bGR4RjRLNk84Wm44ODAzR2tUR0o3MnkrSFVICjJTZkpPV3hyRnVzdysrZ2ZONjBPV0FZbnF5RzkvREttczJsUTFabmw1QU8wUWpxM0NqZkl2ODV4Q2VuQWVsdngKYktrZjFPR1lSNTBHZFl4TGYwMEFaVzhBSFBvOFkvRDBEL2phVXN1OEhsVnFhSWF6SmpTSldpZkFWcFh0cXpaeQp2ZDVWTWRST3diNWdhWWZhRjJVWDZLSlFpemF1K2hzV2ZWOGkzRnNMY2w1YWJmYnkyNUROTlUwVHZYU3V3ckVwCnZBSDNMU2hJeGtRQzU0REc3TDM0WFJ6Q1hkN3U4QkR3U1JaczQzSkxwQ1JKR1RGc0hvNnFPaFdEVFBSa0xDcTUKbGt4bG5FbUNTMFdPWHhRVGRGYUdpN0ZIMVBSLwotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCg==
tls.key: LS0tLS1CRUdJTiBQUklWQVRFIEtFWS0tLS0tCk1JSUV2Z0lCQURBTkJna3Foa2lHOXcwQkFRRUZBQVNDQktnd2dnU2tBZ0VBQW9JQkFRRE5BNTBXRzlKN1BaVGcKVlQ3SWVJeU02a0ZmRlRBTnRaSkdxY1dJQXZQRHZ4amllVzZYdlJDekdKTGdhQzFFbjVHbDlPY2NESVRsL2t1QQpxSUd3VGxqOGU5UDNqcEZjVmhwRGIzUXhyZEdWWHVpN0R6ZEY1SitIaDV2cXVJbFNiakk5ZUl0TjIxL21xLzVxCmQyUVM1VzVWQm5VazFRdUVOQzNEZ1FKSEhJT2l3cmtaUVpOOXBrV3pTdFFZc0RtNUgvZE96cWhlcG5QUkVWZFAKOTVLZ2lVQ0RWbDZza2JBQjduZHBsaWkrZ01YOGlTS2VkWTNUQnlBOGlMRVpPYTQ1c0lJNHJMbWM3WGF2TGlRUwpUQndSMTBrUG9xc2xzWmZvZnRSeFphNmdFdE0veUZNZlUzWGtvZFdRaUFUcVRIRVBOVElveWlwck1YRGNMNVFuCkpJa04yNkNqQWdNQkFBRUNnZ0VCQU1kdUpIbEZSMU1yYkk5dFhVMldOdU05WGFvbzZqM3J5d2VDVHUwb01nalEKOUZ3YTFFSTNZTzlYa0VsTURmMGJYSXViMk5Xb04vK2poNzc0TEhCZFJxTVZzZlMzY3gvbmdsVG5McGpGQllQUQpkNFRBSUh5VkVicTlhQ2JFckpETE1ZUXFweGh0dHJTbHl5KzJSRnM5WkQ3QnNXTEsvQkQyMFMzRmFYblRleG52Cm94Tk42ZFhNMHhZU09MZ2pWNGdEd1VJUUlvNW02TmFadkVHbkNxck9hbDdad0FodmVFeFVpbUU3WUFldVF6dnMKYjE3NWZPOTdLT1hjblAyQm0zUm5SenYwNlNSVmJSdURTdlovamtGUTVJUG9uMUZ6TlJBWm5nYVZ6UldkTUVYbQoySnZPUmptQ3BCbTNvNVpjbUFIaitIQWoxa3l3Qy9SMkhyTU1FeG82Y1lFQ2dZRUE5L2VjZGJKem4zd0pZK0dBCnQ0WS9wRFhnUitpQkNwQnVYTkxubU5VZDJycnJJTXNYWnoyMGlUeVAxL0gwRWl2Q3pLSm9nYnljK2lXUFE2LzIKRVFrcXVIaXoyOGVpaU1DYmUyQVdYUUpTQnpoSy9YM0hWc2V5ckRsRnJyTmZ4SzVxYzVhTUZRbzNGM2tRMVRVUgpyZDczSFkrcWZWMHRHVVhYVlZRd0JkZ2Q3ZmtDZ1lFQTA2ZksrSE0vRS9FQ201TDdKYUoycVgwbmFVMDJzbmxqCjZCbUhDenNVY3EwQUMvdVFrMkJkTFJXbHBlSnU2VXRFU0dIWm1hZ0Fua3VpNTVxdFhTeG1VdGdjOURnTWtleHoKZU9OQkFNQnUrTFRpYVRqeWE0VG5GYjh4YmJaZUtRN2hiYzJQMDdMMjhZRmxxRDg4VDV4VFRpNUs2L3dJclNZWAo2MlJmRytlSEduc0NnWUVBd0JzWUh1TDZ5c01ZcjBYa0o4cWRBWVl2MU9YZkd5VWNLMVBGMDFUQWhWV3NsY0poCnhqMDY0ZHVHZ1VGVTJzTUdidTBmMCtzaEhuYjh6KzdCeng3djl1eWtReEFkN3A1eGxwcXhtS3NVaTcxajg1Ri8KWHM3bHNLSEtSM2QyS1hVS3liUUhvTUZDUHpBdkIwN08vSW94bnJoUDJFSFlqNnpaRDZWaWN4U2swMWtDZ1lBTgo4czNtaDduTmQ2R2pYUkZlRHBIaFk1VVlWSFZaVjdTazFDSFpOS0NKV2l0Wm5zK05WdGx0SWpNVGRwTzJualkyCnl2UUxNMDR2SUc3dzhubWdYVSswLy9jUWhTMFc1TTFMVnphdWRRQWJOZGlCOUxYTkxpb0lmZHdsRGRLd3hBRkoKT2pYVFRzVUZiM0Npb09BNW91UytqMEJ5d3Q1VGd1SXFxaWUyY0JDd1J3S0JnRTM3dWpSN0JHYVI2ZU4xLzh4QwpHUlZ3K2MrSU9yV044YmhONHBGYjNHYU1ELytiaUZmK1BVaXZNMzZzUDAzNnphSno1QnF6NXJILzhKSjZwUmthClUzYzlwKzg2Rk5PU2YrU09KaVhHdko5dkc2Wk5kKzBsUkJXTHRkUUVhZE0va29Sd0c2c3d1bWsyRUROWE9Jd1cKZHV4bFZtdUpENEdhNDU2WDFTejRTMGFiCi0tLS0tRU5EIFBSSVZBVEUgS0VZLS0tLS0K
kind: Secret
metadata:
creationTimestamp: null
name: my-tls
type: kubernetes.io/tls
引用Secret对象
Secret资源在Pod中引用的方式同样有两种
- 环境变量
1.引用Secret对象上特定的key,以valueFrom赋值给Pod上指定的环境变量
2.在Pod上使用envFrom一次性导入Secret对象上的所有key-value,key(也可以统一附加特定前缀)即为环境变量名,value自动成为相应的变量值
- secret卷
1.在Pod上将Secret对象引用为存储卷,而后整体由容器mount至某个目录下key转为文件名,value即为相应的文件内容
2.在Pod上定义Secret卷时,仅引用其中的部分key,而后由容器mount至目录下
3.在容器上仅mount Secret卷上指定的key
注意:容器很可能会将环境变量打印到日志中,因而不建议以环境变量方式引用Secret中的数据
在Pod上引用Secret的示例
- 在Pod上引用Secret资源
apiVersion: apps/v1
kind: Deployment
metadata:
labels:
app: my-dep
name: my-dep
spec:
replicas: 1
selector:
matchLabels:
app: my-dep
template:
metadata:
labels:
app: my-dep
spec:
containers:
- image: nginx:latest
name: nginx
ports:
- containerPort: 80
volumeMounts:
- name: my-secret
mountPath: /etc/nginx/certs/
readOnly: true
volumes:
- name: my-secret
secret:
secretName: my-tls # secret 名称


评论区